 Electronic Arts has announced that Command and Conquer 3 Tiberium Wars will be coming to the Xbox 360. The game continues the Command and Conquer series after a seven year break with the good guys, GDI, fighting the familiar NOD Brotherhood for control of Tiberium.
Electronic Arts has announced that Command and Conquer 3 Tiberium Wars will be coming to the Xbox 360. The game continues the Command and Conquer series after a seven year break with the good guys, GDI, fighting the familiar NOD Brotherhood for control of Tiberium.
Thursday, November 16, 2006
Command and Conquer 3 Tiberium Wars coming to Xbox 360
 Electronic Arts has announced that Command and Conquer 3 Tiberium Wars will be coming to the Xbox 360. The game continues the Command and Conquer series after a seven year break with the good guys, GDI, fighting the familiar NOD Brotherhood for control of Tiberium.
Electronic Arts has announced that Command and Conquer 3 Tiberium Wars will be coming to the Xbox 360. The game continues the Command and Conquer series after a seven year break with the good guys, GDI, fighting the familiar NOD Brotherhood for control of Tiberium.
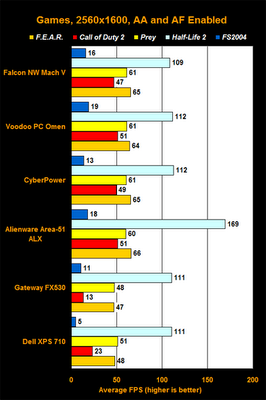
Best Gaming PC for 2006-VoodooPC Omen





 From ExtremeTech:
From ExtremeTech:The Ultimate Game Machine competition in Games for Windows Magazine (formerly Computer Gaming World) is brutal. Every maker of high-end gaming PCs submits their very best, cost be damned. They push everything to the limit, use the very best parts, and really work their butts off to show what the company can do. There are always several great PCs, each worthy of praise and your hard-earned dollars, but there can only be one winner. This year, that winner goes to VoodooPC's Omen, a black monolith of stylish power that managed to edge out even the most impressive competitors.
Wednesday, November 15, 2006
Man uses Digital Audio Player to siphon cash from ATMs
While sniffing out ATM info has been used by tricksters criminals for years, a Manchester-based bloke was trafficking private bank information from various cards to illegally purchase goods -- with the help of DAPs, no less. Although your evil twin could manage to reprogram an ATM to disperse 300 percent more cash than it really should, this fellow secretly attached an (unsurprisingly anonymous) "MP3 player" to the backs of free-standing cash machines in "local bars, bingo halls, and bowling alleys." The device recorded the tones from transactions, which were then decoded and "turned into information used to clone new credit cards." The fellow learned his savvy computing skills from "a friend in Cambridge," and was oddly not caught jacking cash or throwing down on a new HDTV; rather, police caught on to his scheming when they located a counterfeit bank card in his vehicle during a routine traffic stop, which led them back to his presumably disclosing home. While we applaud the ingenuity, the motives are certainly below traditional moral standards, but this certainly isn't the first (nor the last) criminal offense involving DAPs.
Kevin Mitnick's Security Advice
 From Wired:
From Wired:Here's my Top 10 list of steps you should take to protect your information and your computing resources from the bad boys and girls of cyberspace.
-Back up everything! You are not invulnerable. Catastrophic data loss can happen to you -- one worm or Trojan is all it takes.
-Choose passwords that are reasonably hard to guess -- don't just append a few numbers to a no-brainer. Always change default passwords.
-Use an antivirus product like AVG or Norton, and set it to update daily.
-Update your OS religiously and be vigilant in applying all security patches released by the software manufacturer.
-Avoid hacker-bait apps like Internet Explorer and disable automatic scripting on your e-mail client.
-Use encryption software like PGP (pretty good privacy) when sending sensitive e-mail. You can also use it to protect your entire hard drive.
-Install a spyware detection app -- or even several. Programs that can be set to run frequently, like SpyCop, are ideal.
-Use a personal firewall. Configure it to prevent other computers, networks and sites from connecting to you, and specify which programs are allowed to connect to the net automatically.
-Disable any system services you're not using, especially apps that could give others remote access to your computer (like Remote Desktop, RealVNC and NetBIOS).
-Secure your wireless networks. At home, enable WPA (Wi-Fi protected access) with a password of at least 20 characters. Configure your laptop to connect in Infrastructure mode only, and don't add networks unless they use WPA.
Zune MP3 players' opening salvo a dud

"I didn't even know they were there until a customer pointed them out," said sales clerk Jake Brooks.
"I'm sure we have more in a closet in the back somewhere."
By mid-afternoon the store had sold one Zune player and one other person had inquired about them.
The scene was bleaker at a CompUSA store a block away, where the manager said an oversight by Microsoft sales people had resulted in the store not getting Zunes for display.
No apparent harm was done though, said the manager, because no shoppers came asking about Zunes.
Google Maps lets you “Click-to-call”
 From ZDnet
From ZDnetGoogle is about to announce their "Click-to-call" functionality on Google Maps for the United States. Ordering pizza is as easy as searching for "pizza" and clicking "Connect for free" — hopefully in version two they will pay for the food too.
Tuesday, November 14, 2006
Much more coming to Zune??
From ArsTechnica:
See, Zune was designed to connect to the Zune Marketplace wirelessly, it just doesn't do so at the moment. We were admittedly skeptical of such claims, until Bryan Lee, corporate vice president for the entertainment business at Microsoft, decided to get mysterious with the New York Times. Asked if the Zune will ever connect to the Internet, and if it will ever be possible to buy a song that way, Lee responded: "Probably, one day."
Monday, November 13, 2006
Movie studios selling $1.25 DVDs in China to Combat Piracy
From ArsTechnica:
The first studio to announce such a strategy was Time Warner, which said in August that it planned to start releasing cheap DVDs in China in an attempt to fight piracy. The movies were to be released on DVD soon after their theatrical release for about 10 yuan (approximately $1.25) apiece. 10 yuan is close to the typical price for a pirated movie in China. Time Warner hoped that the move would lure customers to buy their DVDs instead of illegal alternatives. The short amount of time between theatrical and DVD release in China was also meant to try to beat pirates in getting the DVDs out as quickly as possible.
Zune: welcome to the anti-social
From ZDnet:
In less than 24 hours, Microsoft will release its latest 'iPod killer' into the wild. The Zune's 'killer' feature being, of course, the ability to share music wirelessly. Where Sony's original Walkman (and subsequently, Apple's iPod) are distinctly anti-social - the bearing of white earbuds being a symbol of solitude - the marketing slogan for the Zune declares, 'welcome to the social'.
However, despite what Redmond would have us believe, the music sharing features of the Zune are anything but social.
David Pogue in his review for the New York Times, hits the nail on the head:
In less than 24 hours, Microsoft will release its latest 'iPod killer' into the wild. The Zune's 'killer' feature being, of course, the ability to share music wirelessly. Where Sony's original Walkman (and subsequently, Apple's iPod) are distinctly anti-social - the bearing of white earbuds being a symbol of solitude - the marketing slogan for the Zune declares, 'welcome to the social'.
However, despite what Redmond would have us believe, the music sharing features of the Zune are anything but social.
David Pogue in his review for the New York Times, hits the nail on the head:
You can play a transmitted song only three times, all within three days. After that, it expires… This copy protection is as strict as a 19th-century schoolmarm. Just playing half the song (or one minute, whichever comes first) counts as one “play.” You can never resend a song to the same friend. A beamed song can’t be passed along to a third person, either.That's right, 'a beamed song can’t be passed along to a third person', which, in my mind, is as social as telling a friend about a great place to eat out, on the sole condition that they don't tell anybody else. According to Pogue, Microsoft is marketing the viral 'potential' of the Zune, as a way for unsigned bands to promote their music:
What’s really nuts is that the restrictions even stomp on your own musical creations. Microsoft’s literature suggests that if you have a struggling rock band, you could “put your demo recordings on your Zune” and “when you’re out in public, you can send the songs to your friends.” What it doesn’t say: “And then three days later, just when buzz about your band is beginning to build, your songs disappear from everyone’s Zunes, making you look like an idiot.”
Subscribe to:
Comments (Atom)
